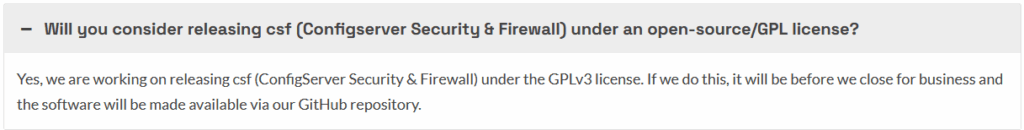
Running immich in docker (with TLS/SSL)

Fed up with the notifications from google that your disk space is getting full? Then host your own photos.google.com, but it’s called immich (image, duh). You’ll need a machine with docker installed and plenty of disk space for what you want to save.
Now, apart from your photos you’ll need 3 files, .env and docker-compose.yml, and an empty file in ./data/vhosts with the name of the vhost in you want your immich site to be available on. This file will be used to tell Let’s Encrypt what the hostname is you want an SSL certificate for. I’ve mounted a disk specifically for storing my data on /var/store/immich.
Note that in the machine learning section, rocm is for Radeon.Check the original docker-compose.yml file for the name for NVidia. Read More